
The creator of a website where UQ students review courses and lecturers has blamed foreign hackers for a script that mined cryptocurrency on visitors’ computers.
A member of the UQ Computing Society discovered the malicious script last Tuesday, when the website caused his CPU to run at 100% capacity.
A look at the website’s source code revealed a script called Coinhive, which uses a visitor’s computer to mine the ‘Monero’ cryptocurrency, often without the visitor knowing.
It remains unclear how many visitors were affected by the code, which appeared on UQ Review during the holidays, when many students are likely considering their course options for 2018.
Luke Beacon, the creator of UQ Review, told Semper that the website has been popular for its informal approach to course reviews.
“We ask questions like ‘do you need the textbook?’ rather than ‘I had a clear understanding of the aims and goals’,” he said.
The News Breaks to StalkerSpace
News broke about the malicious script late on Thursday night in UQ Stalkerspace.
Students immediately raised questions about whether the University or the Student Union was responsible for the site.
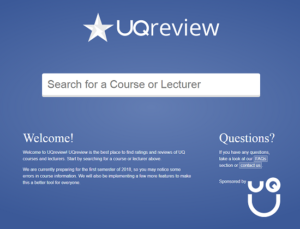
But, despite using the UQ name and the UQ Union logo, the website does not have a relationship with either organisation.
UQ Union President Jeremy Lwin told Semper that “UQU provides no funding to UQ Review and is not involved in its operations”.
“Our records show that UQU executives met with Mr Beacon twice in 2014, but we have had no relationship with the website since then,” Mr Lwin said.
“For students who are looking for more information on a course, we recommend reviewing the official SECaT evaluations made available on the UQ Union website,” he said.
A spokesperson for the University of Queensland told Semper that access to UQ Review is currently denied while on the UQ network.
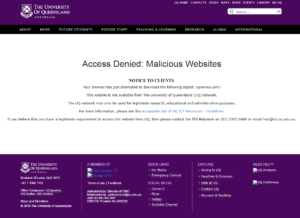
“UQ uses the FortiGuard web filtering service. FortiGuard classified this site as malicious at 05:45:29 on Sunday 17 December,” the spokesperson said.
“Usually FortiGuard classifies sites as malicious through a combination of public reports and other malicious site listings such as the Google Safe Browsing project,” she said.
Mr Beacon said he was “disheartened” that access had been denied, but understood that “[UQ] probably don’t want their CPU and power to be used to mine cryptocurrencies for some foreign hacker”.
The Future for UQ Review
Mr Beacon said he was taking steps to increase the security of the site, by “installing an SSL certificate to force HTTPS, enabling a geo IP blocker to only allow Australian traffic, and [auditing] all inputs that are susceptible to injection attacks”.
“There has been a lot of attacks recently from Russian and Asian IP addresses that have caused large CPU spikes on my host – mostly to submit spam reviews,” Mr Beacon said.
“This is the first [time] I’ve seen code injected into the source,” he said.
Mr Beacon said he will contact UQ IT services to discuss restoring access to the site when the security upgrade is complete.
Views: 561
